UPDATE
Startcom is now at this URL. And although the certs are still free, they no longer work with things like Chrome, or Safari, or Firefox… which doesn’t leave much 😉
I’m still investigating other free SSL services…
Why do you need a SSL certificate?
Short answer: to enable encryption! For example, if you are running a web-site and *any* part of it requires authentication, then you should enable SSL. For the whole site. No, you can’t just enable SSL for the authentication piece and then use cookies, because the session can be hijacked. No session hijacking is not hard, here is a Firefox plugin that will do it: Firesheep
Why you need a valid certificate – or – why you can’t use a self-signed certificate
A SSL certificate serves two important functions. The first, which you already know, is that it enables encrypted communication. But the second, and often overlooked function is that the SSL certificate verifies the identity of the other party you intend to communicate with. This is very important, easily as important as the encryption itself. Without the verification step, shady people could fool your computer into passing data thru a third party in an attack vector referred to as a man-in-the-middle attack.
But how does this verification work? The short answer is digital signatures and trust. When you connect to an encrypted web site, the server sends you a certificate that is signed by a third party. Your browser then verifies this signature against a local database of certificate identities, all of which your browser trusts. (Note: Why does your browser trust them? The author of the browser trusts the certificates and so included them with the install package). If the certificate has a valid signature from a third party that your browser trusts, then it will trust the remote server.
If you imagined the servers having a friendly conversation, it might go like this:
you: “Hey are you Bob.com?”
Bob.com: “I sure am – you can see here that Joe.com trusts me – I have his signature here.”
you: “Let me check – yup, that’s Joe.com’s signature all right. If he trusts you, you must be ok”.
Bob.com: “Great – let’s go off the record!”
That’s how a valid certificate works. But when you want to run your own site, you have to get Joe.com to trust you, which usually involves money. After all, Joe.com wants to get paid for going to the trouble of verifying that you really are Bob.com.
Of course, you don’t have to use a valid certificate; you can self sign the certificate instead. This just means that you create your very own certificate authority and then add your own signature. Now the conversation goes like this:
you: “Hey are you Bob.com?”
Bob.com: “I sure am – you can see here that I trust myself – I have my signature here.”
you: “Uhhh. Let me throw an error up on my user’s screen. Well, he clicked thru the warnings, so… I guess you must be ok.”
Bob.com: “Great – let’s go off the record!”
This does enable encryption, but it’s going to throw a lot of your users off since they with probably not fully understand why they are getting the error. Of course if you are just running a site for yourself or some friends, this is probably not a problem, and in fact in that case you can install the certificate (by trusting it permanently) and then you won’t get errors anymore.
This is what I did for years for my own sites. But it always bothered me. Well, and it causes weird problems that can waste a lot of time to troubleshoot. For example, the Flash uploader for WordPress just does not work with a self signed certificate (See: No-SSL-Flash-Upload). But, the inconvenience was never serious enough to pony up the $15/yr (or more!) for the privilege of having a valid certificate.
Enough already – Where do I get one?
So, about once a year I got annoyed with self signed certificates and asked google to help me out. And this time, there was a hit! Here it is:
StartCom Free SSL Certification Authority
And why is it free? I love this: “Because we believe in the right to protect and secure information between two entities without discrimination of race, origin and financial capabilities.”. Yes! I love these guys already!
What you get for free is a basic SSL certificate. In the case of a certificate for a web server, you get protection on the base domain name and one name, for example “alleft.com” and “www.alleft.com”. This is a nice feature because you can run SSL on the domain name and do a redirect to www without breaking encryption. You can also get a S/MIME cert for email, a certificate for XMPP, and an Object Code Signing cert. Did I mention it’s free?
The setup process was a little bit convoluted, but not impossible to follow. Basically, after setting up your account the website will install an Authentication Certificate into your browser so you won’t need to remember a username and password. However, if you want to login from another computer, you’ll need to export this certificate and copy it to the new computer.
Once your account is setup, you then need to prove you own the domain you want a certificate for using the “Validation Wizard” – there are the standard tests available: email address, domain name, personal identity, etc. Then you can go thru the “Certificates Wizard” and get your key and cert setup.
I can confirm that the certificate is real and has been working great – any you can try it for yourself by hitting this site with https if you like. It seems that the intermediate cert is not recognized by my Android phone, which is unfortunate, but will likely be resolved in future versions of the built-in browser.
So… Now you don’t have an excuse to not use encryption!




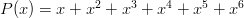
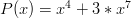
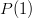 is the number of sides on the die. Also notice that this representation encapsulates the probability of a specific roll, i.e., the probability of a die
is the number of sides on the die. Also notice that this representation encapsulates the probability of a specific roll, i.e., the probability of a die 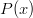 rolling a “n” is:
rolling a “n” is: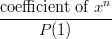
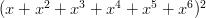
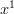 is zero, the coefficient of
is zero, the coefficient of 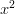 is one, and the coefficient of
is one, and the coefficient of 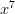 is six (0/36, 1/36, and 6/36).
is six (0/36, 1/36, and 6/36).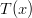 and
and 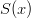 such that:
such that: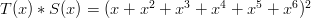
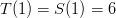
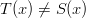
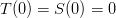
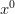 term, which is the same as saying that the dice have no blank sides.
term, which is the same as saying that the dice have no blank sides.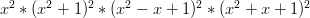
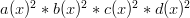
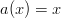
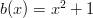
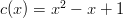
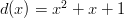
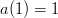 so multiplying by
so multiplying by 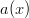 will not change the number of sides on the die. Also notice that if we put both
will not change the number of sides on the die. Also notice that if we put both 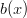 ,
, 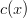 or
or 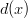 would incur a monomial). Thus, both
would incur a monomial). Thus, both 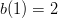 and
and 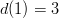 , whose product is six. Also notice that
, whose product is six. Also notice that 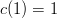 . Thus, if we want
. Thus, if we want 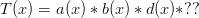
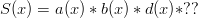
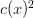 . If we put a
. If we put a 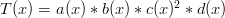
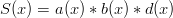
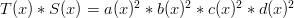 . How about condition #2? Well,
. How about condition #2? Well, 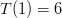 and
and 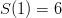 so that looks good. Clearly,
so that looks good. Clearly, 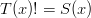 so condition #3 is ok. Finally, neither term has a monic, so
so condition #3 is ok. Finally, neither term has a monic, so 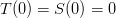 and neither die has a blank side.
and neither die has a blank side.